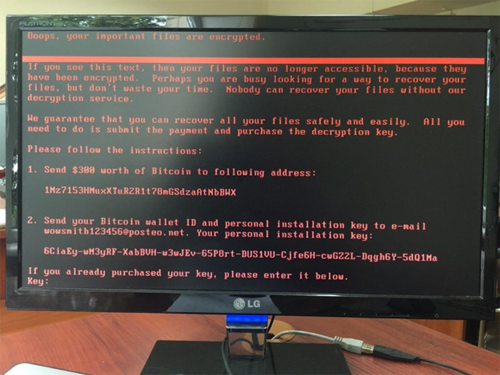
Petya Ransomware Spreading Rapidly Worldwide, Just Like WannaCry
The WannaCry ransomware is not dead yet and 2nd wave of ransomware attack based on the recent SMB exploit is here. A new variant of Petya ransomware, also known as Petwrapworks very differently from any other traditional ransomware. Instead of encrypt files on a targeted system, Petya reboots victims computers and encrypts the hard drive’s Master File Table (MFT). Which means restricting access to the full system.
Don’t Pay Ransom, You Wouldn’t Get Your Files Back.
The email account for accepting ransome payment was shut down. Hence, infected users are advised not to pay the ransom because hackers behind Petya ransomware can’t get your emails anymore.
[divider]
What to do now:
- Make sure your endpoint security provides exploit protection: For Kaspersky users, make sure that the Kaspersky Security Network and System Watcher components are turned on.
- Manually update the antivirus databases immediately.
- Install all security updates for Windows. The one that fixes bugs exploited by EternalBlue is especially important. Visit here for the step by step process.
- Thoroughly check emails containing attachments (invoices, office, script or executable files) and to scan them using a virus check.
- Block inbound connections on TCP Port 445.
- Create and maintain good backups so that if an infection occurs, you can restore your data.
If you need further assistance on WannaCry/Petya or Ransomware protection generally, Do contact us at 03-80752050 or email support@internetnow.com.my