MalwareHunterTeam discovered two new Matrix Ransomware variants this week that are being installed through hacked Remote Desktop Services. While both of these variants encrypt your computer’s files, one’s a teeny bit advanced than the other by overwriting the free space on the C: drive.
The differences are described below.
Variant 1: [Files4463@tuta.io]
As it is encrypting your files, this variant opens 2 windows (Encrypting Screen and Network Scanning Screen, respectively) that display the status of the infection.
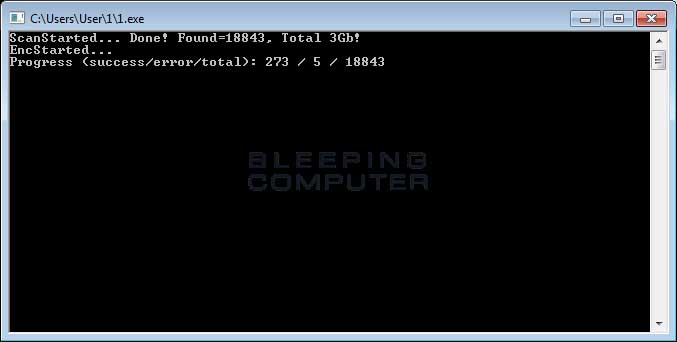
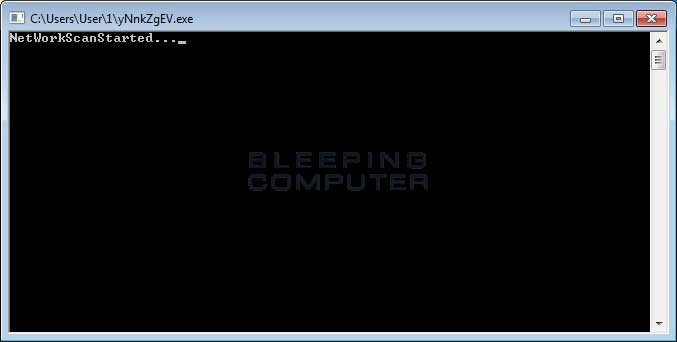
Once encryption of files is complete, it would then encrypt the file name and then append the [RestorFile@tutanota.com] extension to it while simultaneously, dropping a ransom note named !ReadMe_To_Decrypt_Files!.rtf in each folder that is scanned and changing the desktop background to the following image.
Variant 2: [RestorFile@tutanota.com]
While it also opens 2 windows (Encrypting Screen and Network Scanning Screen, respectively), you can notice far greater logging is shown in this variant compared to the previous one.
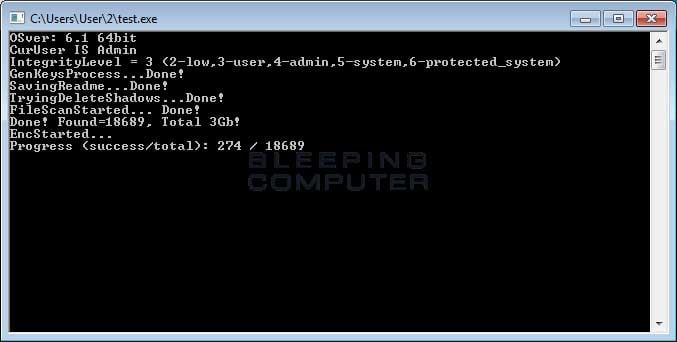
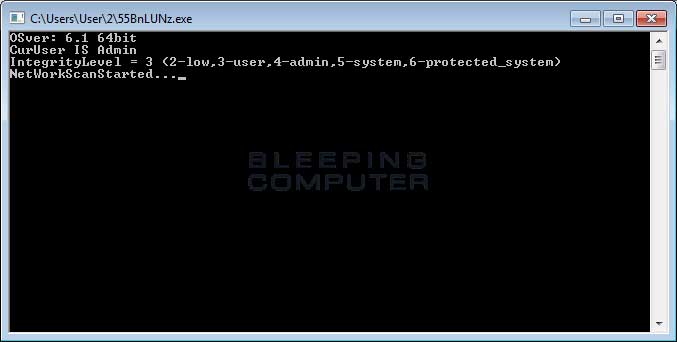
Like the First Variant, this variant also encrypts the file name while appending it to
[RestorFile@tutanota.com] extension. At the same time, it also drops a ransom note #Decrypt_Files_ReadMe#.rtf in each scanned folder while changing your background to the following image.
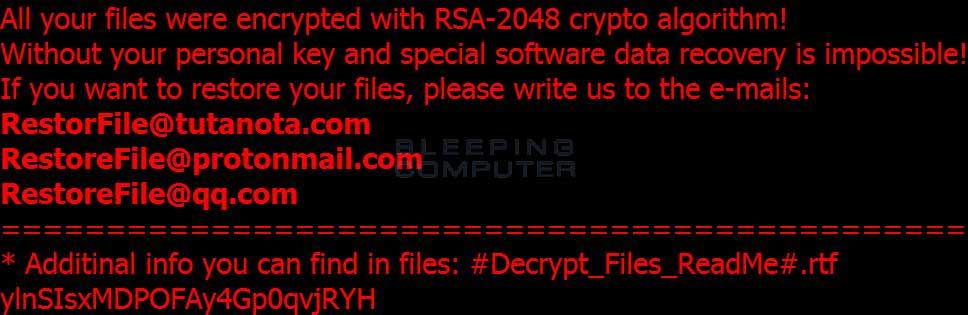
Unlike the previous one, this variant continues to overwrite the free space on your C: drive by executing cipher.exe /w:c command which makes it impossible for victims to recover their files by using recovery tools.
While both these variants cannot be decrypted for free, steps can be taken to protect yourself from these new variants.
- Always have a reliable and tested source of backup. BackupAssist (v.10), is reasonably priced while being the ONLY backup software that comes with an Anti-Cryptor tool called CryptoSafeGuard.
- Do Not Open Remote Desktop Services to the Public via direct connection to the Internet. Instead ensure all connection to the Internet goes through VPN’s like SOPHOS Firewall (XG Series), making it accessible to those who have VPN accounts on your network.
- Have a security software that incorporates behavioral detections and not just signature detections or heuristics, like Kaspersky Endpoint Security for Business Select.
- Use a strong password that contains symbols, numbers, and both uppercase and lowercase alphabets, The stronger your password the harder it becomes for Cyber Criminals to find a backdoor into your system by using brute force.
- Obey Common Security Habits:
- Do not open attachments from unknown sources
- Scan all attachments before opening them
- Ensure your PC’s software and programmes are always up to date.
- Never reuse the same password on multiple sites.
Click here to get a NO-OBLIGATION QUOTE from us
Read more at https://www.bleepingcomputer.com/news/security/new-matrix-ransomware-variants-installed-via-hacked-remote-desktop-services/.

