Change in Attack Strategy
PAST

Malware
• Organisations had to only worry about malware.
• Malware are malicious software which spreads through the network, removable devices and email.

Hacking
• Hacking is manually done by cybercriminals to try to find some weakness in your system
• This weakness could be a bug in your software – i.e. a vulnerability
• Or because of bad security policy – i.e. weak passwords or substandard protocols.
PRESENT

Targeted Attack
• Uses a combination of both hacking and malware to achieve monetary gain (e.g. through data theft or ransom payment)
• Hacking is used to get into the system, malware is used create backdoor into your network or also encrypt your data (Ransomware)
Challenges InsightNow! Can Address
Our Approach
Cybersecurity Transformation Kit
Revisiting your Cybersecurity Playbook – and finding where to begin your transformation journey – isn’t easy. We’ve created this Transformative Toolkit to help you navigate the landscape and gain some insight on where to start your transformation.
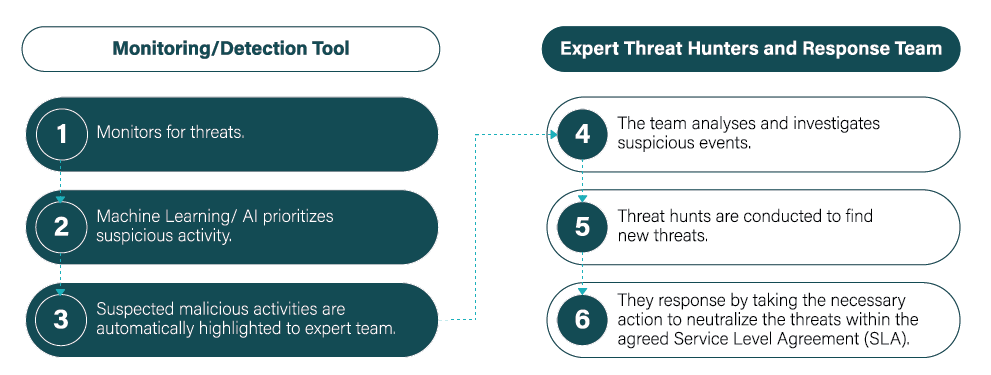
Threat Notification Isn’t the Solution – It’s a Starting Point!