Threat Notification Isn’t the Solution – It’s a Starting Point
Most organisation pay for antivirus and/or endpoint protection but do not actively monitor its status. Most antivirus and endpoint, simply notify you of attacks and/or suspicious events. Then, it’s up to your IT team to manage things from there. With InsightNow!, organizations are backed by an elite team of experts who take targeted actions to neutralize even the most sophisticated threats within the agreed Service Level Agreement (SLA).
Change in Attack Strategy
PAST

Malware
• Organisations had to only worry about malware.
• Malware are malicious software which spreads through the network, removable devices and email.
SOLUTION
It can be detected by antivirus (Sophos Intercept X Advanced), firewall (Sophos XG).

Hacking
• Hacking is manually done by cybercriminals to try to find some weakness in your system
• This weakness could be a bug in your software – i.e. a vulnerability
• Or because of bad security policy – i.e. weak passwords or substandard protocols.
SOLUTION
Review and update protocols and passwords, regularly.
PRESENT

Targeted Attack
• Uses a combination of both hacking and malware to achieve monetary gain (e.g. through data theft or ransom payment)
• Hacking is used to get into the system, malware is used create backdoor into your network or also encrypt your data (Ransomware)
SOLUTION
iNSIGHTNOW – Managed Security Services. 24×7 monitoring, threat hunting and responding by a team of experts.
Targeted Attack is Bigger Problem vs Normal Ransomware attack because:
- They disable your backup.
- They disable your antivirus before executing the ransomware – via the use of exploits and zero-day malware
- They remove their tracks, so you do not know how they gained access.
- They maintain a foothold inside your network (also known as Advanced Persistent Threat – APT), where they stealthy undetected on at least one of your systems for an extended period.
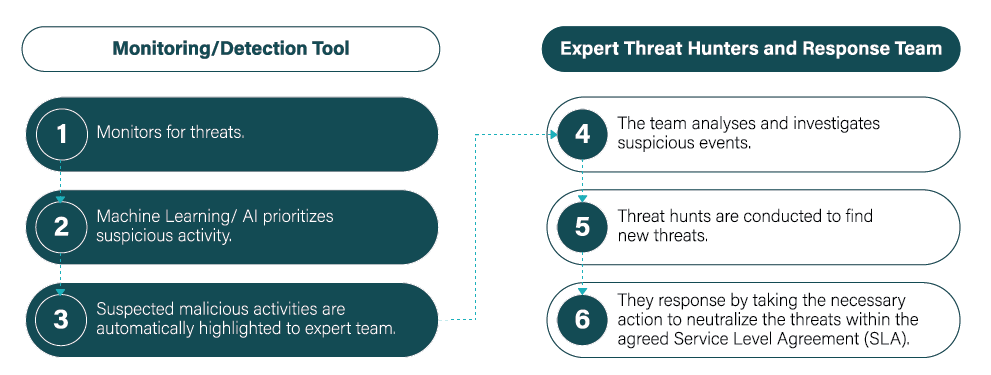
Challenges InsightNow! Can Address
Our Approach
Complete Control and Transparency
We do the work, but you (organisations) own the decisions. This means you control how and when potential incidents are escalated, what response actions (if any) you want us to take, and who should be included in communications. InsightNow features three response modes, so you can choose the best way for our team to work alongside you during incidents:

Lack of security skills
Most SMEs’ will find it a difficult proposition given their resource limitations to train and set up a dedicated security team that can focus on full-time threat hunting, monitoring and response.

Challenges
Challenges when deploying complex endpoint detection and response (EDR) solutions – which are usually not being maximized due to a lack of time, skills, and funds to train personnel to handle the tools.

Sheer volume of alerts security and IT teams regularly receive
We handle containment and neutralization actions and inform you of the action(s) taken

High-Fidelity Detection
We combine deterministic and machine learning models to spot suspicious behaviors and the tactics, techniques, and procedures used by the most advanced adversaries.

Proactive Defense
Combining threat intelligence with newly-discovered indicators of compromise identified through threat hunts, Intercept X proactively protects your environment.

Elite Expertise
Our highly-trained team of engineers has your back 24/7, investigating anomalous behavior and taking action against threats.
Continuous Posture Improvement
Every hunt, investigation, and response action results in decision-driving data that is to enhance configurations and automated detection capabilities.
Cybersecurity Transformation Kit
Revisiting your Cybersecurity Playbook – and finding where to begin your transformation journey – isn’t easy. We’ve created this Transformative Toolkit to help you navigate the landscape and gain some insight on where to start your transformation.
Threat Notification Isn’t the Solution – It’s a Starting Point!